Preventing Unwanted Reverse Engineering of Microchips
 |
| Professor Emre Salman |
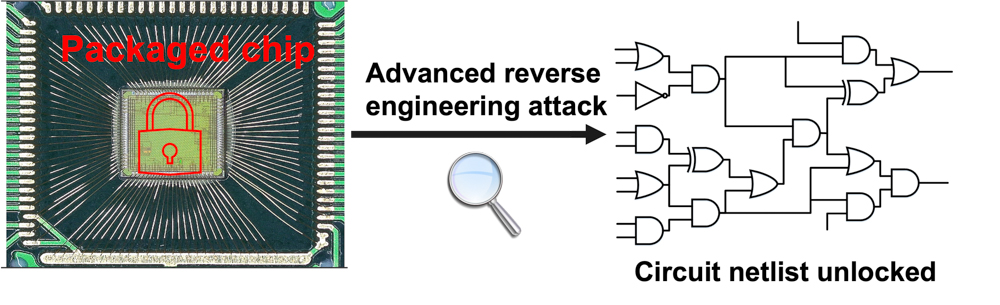
Prof. Emre Salman and doctoral candidate Ivan Miketic recently published a unique obfuscation technique to make digital computer chips more resistant to reverse engineering. Why is this important? One of the key security issues for chip design companies is reverse engineering. Reverse engineering involves several physical attacks to the chip to regenerate the circuit netlist. The “netlist” is the description of a circuit including the gates, inputs, outputs and their interconnections. Once the netlist is obtained, counterfeit designs that are not authentic can be fabricated. This is typically referred to as Intellectual Property (IP) theft. Reverse engineering poses a significant economic risk to the semiconductor industry due to lost profits and reputation. It also presents a considerable risk to consumers and private data.
The research community has actually developed several obfuscation techniques to protect circuits against reverse engineering or make reverse engineering attacks more difficult. These techniques, however, typically introduce significant overhead such as additional chip area and power consumption. In their work, Salman and Miketic leverage adiabatic circuits and some of their unique characteristics to develop a novel circuit obfuscation technique. The protected circuit is highly resistant against reverse engineering attacks with minimal overhead.
 |
| Ivan Miketic |
The Stony Brook University team’s method is lightweight, meaning that it has much less overhead than conventional obfuscation techniques, while still achieving a high degree of protection against reverse engineering. The proposed technique is also more resistant to some of the advanced attacks since it is based on adiabatic circuits. These kinds of circuits are different than conventional approaches as they rely on certain phase differences among the gates for correct operation. Salman and Miketic use those phase differences in their technique to their advantage to obfuscate the circuit netlist. Thus, even though a reverse engineer uses sophisticated techniques to obtain the layout of the chip, they cannot figure out the real netlist without knowing what the true phase differences are.
Indeed, attackers can come up with advanced formal techniques to diminish the efficacy of circuit obfuscation techniques. Thus, the main objective of the research community is to make these attacks increasingly more difficult. Since the Stony Brook’s team approach relies on adiabatic operation, most of these advanced formal attack methods do not yet exist for these kinds of circuits. Salman and Miketic believe that their recent paper will contribute to the emergence of new research topics at the intersection of adiabatic circuits and reverse engineering.
How would the approach be used in practice? First, the digital circuit needs to be designed based on adiabatic principles rather than conventional static CMOS. There is limited design automation capability for such circuits. However, not the entire chip needs to be adiabatic, only the parts of the chip that need the most protection. It can even be possible to have these blocks ready as hard IP (i.e. already designed so it can be ‘inserted’ into the chip). Since Prof. Salman has had industry sponsorship for this research, he already sees some interest in adapting this idea for the security layer of the chip.
Prior to this project, Salman and Miketic had already been working on adiabatic circuits. As part of another project, they developed a method to use adiabatic circuits in RF-powered applications to achieve an order of magnitude reduction in power consumption. As they gained a deeper understanding of the operating principles of adiabatic circuits, they intuitively thought that it would bring some interesting advantages in the field of hardware security.
When Prof. Salman and Ivan Miketic first had the idea, they were excited about it as it was a very different approach than existing techniques and had the promise to deliver good results. As they started working on it, they faced several difficult issues to overcome, which they didn’t anticipate at the beginning. The research infrastructure Prof. Salman has in his lab as well as close communication with his students helped facilitate this research.
The Salman and Miketic paper was published at IEEE Transactions on Very Large Scale Integration Systems in May 2021 https://ieeexplore.ieee.org/abstract/document/9440196 . This research was co-funded by Semiconductor Research Corporation (SRC) and National Science Foundation (NSF).